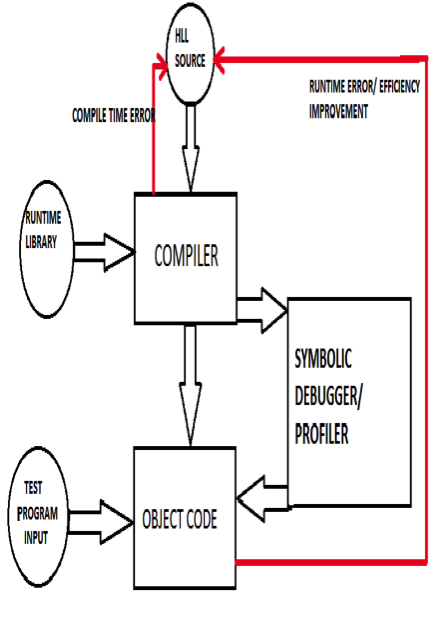
Figure 1. Side-by-side comparison of software compilation and hardware synthesis.
 ENPM 643/ENSE 623 Projects, Fall Semester, 2014
ENPM 643/ENSE 623 Projects, Fall Semester, 2014
[ Project 1 ]:
Verification and Validation of the Pointing Control System for PIPER
[ Project 2 ]:
Using Markov Chain as a Formal Model to Evaluate Performance of
Healthcare Process in Diabetic Management Health Complication
[ Project 3 ]:
Validation of Social Media Business Methodology
[ Project 4 ]:
Using JUnit tests to verify and validate a Course Management System
[ Project 5 ]:
Decision Support Model for Physical Protection System Validation and Verification
[ Project 6 ]:
Requirements Management and Verification for Manufacturing Processes
[ Project 7 ]:
Project Proposal: Hardware Design Verification using Verilog FPGA
[ Project 8 ]:
Verification and Validation of Automated Traffic Control System Project
[ Project 9 ]:
Verification and Validation in the Smart-Grid Environment
[ Project 10 ]:
Validation and Verification of Packaging Strategies for Humanitarian Aid/Disaster Relief (HA/DR) Response
[ Project 11 ]:
Water Distribution System Security
[ Project 12 ]:
Validation and Verification for Unmanned Underwater Autonomous Vehicles
[ Project 13 ]:
A Framework For Natural Language Processing in Requirements Engineering
[ Project 14 ]:
Verification and Validation of Parcel Router System
[ Project 15 ]:
JUnit Testing for a Predictive Analytics System
Title: Verification and Validation of the Pointing Control System for PIPER
Authors: Jared Hansen and Tim Middleton
Abstract: The Primordial Inflation Polarization Explorer (PIPER) is a mission being formulated, implemented, and operated by the National Aeronautics and Space Administration (NASA). PIPER is a balloon borne instrument that will attempt to uncover evidence of gravitational waves. PIPER has several complex entities that support its project efforts, but for the sake of this class we will focus on the Pointing Control System (PCS). The PCS is essential to PIPER because it provides the overall control of the payload as it floats 100,000 feet in altitude.
Our project presents a detailed overview of the verification and validation activities and techniques that will be used to evaluate PIPER's Pointing Control System.
In keeping with the NASA Engineering Lifecycle, this project will aim to prepare for a Critical Design Review (CDR). The CDR demonstrates that the maturity of the design and development effort is appropriate to support proceeding with full-scale fabrication activities and that the project is on track to meet all functional and performance requirements within the identified period of performance. This includes the development of a Verification and Validation test plan.
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title: Using Markov Chain as a Formal Model to Evaluate Performance of
Healthcare Process in Diabetic Management Health Complication
Authors: Iakovos Katsipis and Jonathan Candari
Abstract: Electronic Health Record (E.HR) is a system that is currently used by health care providers (e.g., health care insurers, hospitals and clinics). The current E.HR system is static database and does not provide comprehensive picture of the risk especially associated with critical conditions such as diabetes. The limitation of the current E.HR system is that there is no early signal that could track the population's risk condition so that a proactive health or behavioral intervention can be introduced. The intent of this project is to present a formal systems engineering model of the risk prediction particularly for diabetes management using Markov Chain. In this project, we will also research on telemedicine technology that will be used for the systems-level design and implementation strategy. Test and validation will be carried out by comparing the traditional processes with the proposed system.
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title: Validation of Social Media Business Methodology
Authors: Isabelle Shuggi and Christa Rogers
Abstract: Our project will attempt to validate the social media methodology we developed last semester, when we analyzed the impact of social media on modern business methodologies. In order to validate our model we plan to compare our model with other existing models. Then we will determine if there are components missing from our model as well as other models. Determination of missing components will be done through a comparative analysis of models and analysis of current business practices.
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title:
Using JUnit tests to verify and validate a Course Management System
Author: Anicet Ndjiya, Songong Garique and Jeremy Feldman
Abstract: The goal of this project is to write JUnit tests to verify and validate a Course Management System built in a previous course. The Course Management System is a Java project, which started in the ENPM613 Software Design course during the Fall 2013 semester. The goal was to design and implement a system that allows instructors to post announcements, assignments, quizzes and lecture notes, and that also allows students to view all the course material while having the ability to send email messages.
The system was implemented, but not a lot of effort was taken to verify and validate it. We will use the unit-testing framework for the Java programming language called JUnit to write test classes, in order to verify and validate that the requirements for the system have been met.
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title:
Decision Support Model for Physical Protection System Validation and Verification
Author: John Johnson and Soroush Bassam
Abstract: This project will develop a working decision support system and validation model for physical security system leveraging building information modeling (BIM) and systems engineering approaches through ontology-based decision making and state-modeling validation.
Modern buildings are increasing in complexity as highly intricate and adaptable systems that dynamically control environments, monitor and minimize energy use, maximize usability and reuse-ability of building spaces, and provide secure transportation of people, energy, material, and information. In response, systems engineering approaches are now becoming commonplace to meet these challenges through the use of building information modeling (BIM) - technology capable of providing three-dimensional models of buildings that can identify building structural components and/or spaces that are tagged and backed by database software containing building-component information. While BIM is continuing to mature and grow in use, the information models provide a platform to enable what have been termed as "BIM-aware applications" that can leverage the three-dimensional databases to provide decision support for building design and management. Physical security is a critical and under-served area of design and management of buildings, with losses due to economic espionage estimated at $5 trillion dollars a year (nearly twice the tax revenue) much due to breaches in physical and/or physical-cyber security. In current state-of-the art practice, builders consider Physical Security post-design and often requiring significant on-site inspection to develop detailed formal analysis to ensure physical security requirements are met by physical security designs.
This project will propose new methods to integrate Physical Security into the design and management process through ontology-based modeling and control algorithms that leverage BIM models to perform formal analysis of physical security system designs. This work will build on the modeling methods developed in ENSE622/ENPM642 to evaluate building information models for physical security designs, adding decision support capabilities Excel and Java-based decision engines (e.g., Jena), as well as validation through the software labelled transition system analyser (LTSA) for modeling and prevention of potential flaws in a building's Physical Security Design.
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title: Requirements Management and Verification for Manufacturing Processes
Author: Pedro Pena and Christopher Brothers
Abstract: As systems continue to grow more complex with increasing number of components and functionality, the number of manufacturing and acceptance test requirements grows as well. The management of these requirements is critical to the success of the product. Mismanagement of these requirements could potentially lead to a defective or discrepant product being implemented in the field. Ultimately, this defective product could lead to a field failure and in certain applications could lead to the loss of life.
This project focuses on a requirements management database that ensures that the correct manufacturing process is developed in order to satisfy all customer requirements. The database will provide visibility to how each requirement is implemented and satisfied in the manufacturing process. Non-valued added process will also be highlighted in this database to ensure the manufacturing process is implementing lean principles. Ultimately this database will provide early alignment and verification between the manufacturing process and the customer needs
References
Midterm Presentation: Scheduled for November 4, 2014.
Class Presentation: Scheduled for ....
Title: Project Proposal: Hardware Design Verification using Verilog FPGA
Author: Sana Awan and Senay Tekle
Abstract: With current chip complexities at 50 million active devices and growing, it is no longer possible to design hardware using schematic based methods. Inevitably, design must now come almost exclusively from high-level specifications and synthesis. It is an area where methodologies are not well-established, yet the tools are evolving rapidly to keep up with the headlong expansion of chip complexities. This evolution is parallel to that taken by software engineering a generation ago: few people want to look at the assembly code produced by software compilers; debugging is preferentially done at the source level. In the same way, when description of something as simple as an alarm clock specification is expanded from by the synthesizer from less than two pages of high level source code to more than 40 sheets of gate schematics (Paul Franzon, Synthesis of Digital Systems) then we would prefer to debug it from the former rather than the latter. To summarize: state-of-the-art hardware compilation is not at all like that of software. The two are compared in Figure 1.


Figure 1. Side-by-side comparison of software compilation and hardware synthesis.
In hardware synthesis, there are more stages to the process, in each of which further errors may be uncovered. The first stage is simulation of the high-level source specification to determine if the overall design is sound. The source code is then presented to the analysis and elaboration stages of the synthesizer where further errors may be detected. (A Synthesizer converts verilog Hardware Descriptive Language to circuit netlists consisting of LUTs, flip-flops and RAM blocks). At the present state of the art, it is very possible for source accepted by the simulator to be rejected by the synthesizer and vice versa. Next, the design is presented to the compile phase of the synthesizer. Only after this, and when the design has been fitted onto a chip, will the true delays in the circuits and connections be known. At this point, the design must be submitted again to simulation and possibly a formal verification tool (called testbench). By the time the design is actually downloaded to be fabricated into silicon, it is fervently hoped that no design errors remain. However, unlike software in which the copies are to all intents and purposes perfect, hardware replication errors may still occurin the fabrication process; this necessitates another layer of testing by on-or-off chip facilities. It is possible to use the same testbench program for all of the testing stages provided this stimulates and senses only the circuit nodes available on the external pins.
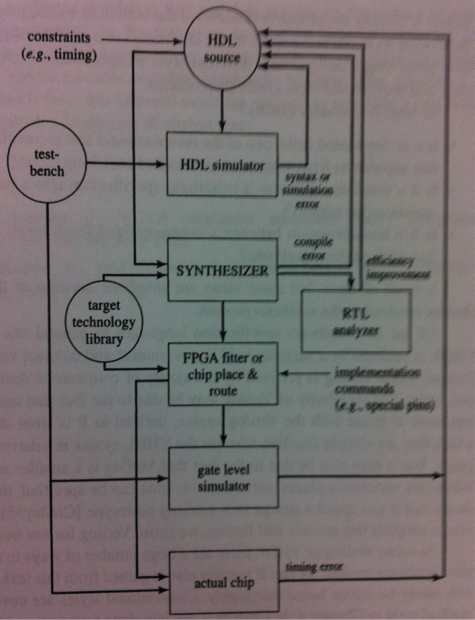
Figure 2. Detailed FPGA design flow from design entry through implementation.
Throughout this process, the high-level source is the single reference point for understanding and correcting the design. The style of this specification, called ‘writing style’ ranges from pure behavioral(C language-style) to pure structural (logic gate-style) or any gradation in between. It has therefore much to do with the quality of the final synthesized results.
In this project, we not only present the different writing styles for hardware specification, but also take the reader through the hardware design cycle for Finite State Machine based sequential circuit using Verilog Hardware Description Language (Verilog HDL) and implemented on a XILINX Spartan-3 Field Programmable Gate Array (FPGA) Board.
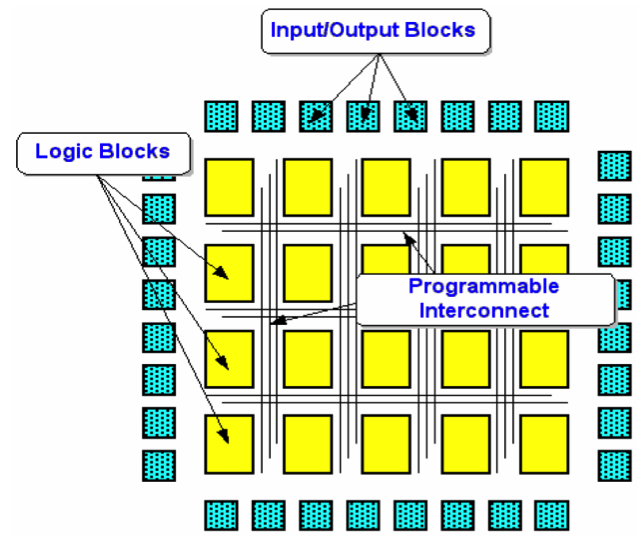
Figure 3. Basic FPGA architecture.
The XILINX Spartan-3 FPGA is typically SRAM-based and therefore volatile. It consists of an internal array of configurable Complex Logic Blocks (CLBs) and a ring of programmable input/output blocks connected together via programmable interconnection. Its logic characteristics can therefore be changed and manipulated or stored through programming. This powerful reconfigurability feature of the FPGA can be exploited in the design verification process, thereby reducing time-to-market if the design specifications change for some reason during the design cycle.
References
Midterm Presentation: Scheduled for November 4, 2014
Class Presentation: Scheduled for ....
Title:
Verification and Validation of Automated Traffic Control System Project
Author: Bryan Janaskie and An Nguyen
Abstract: As modern systems become increasingly complex and are expected to handle higher densities of information, they have begun to rely heavily on automated control systems. Examples of these advanced systems include the automated warehouse delivery system for warehouse materials management and Amazon's drone delivery concept. These systems are ground breaking and pave the way for wider implementation of automation. However, one of the major challenges that are common to these systems is their ability to execute automated traffic flow via collision avoidance, which is one of the key components to ensure successful and safe implementation of these advanced automated systems.
This research project will investigate such collision avoidance system using a realistic application of traffic congestion at an intersection. In this project, the team will investigate a network of automated vehicles that requires careful planning to ensure the safety of the vehicles passengers, while safely and effectively maintains traffic flow with minimal delays or roadblocks. This project will focus on in particular the verification and validation of a safe method for vehicles to pass through an common intersection.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: Verification and Validation in the Smart-Grid Environment
Author: Ammaribn Nada and Andre Yamasaki
Abstract: The goal of this project is to present a formal systems engineering model of the risk predication in implementing a micro-grid through the use of modeling and simulation.
This micro-grid involves a power system enabled with communication and networking infrastructure to an unprecedented level. This introduces many sophisticated features including energy-resource sharing, distribution, ad load balancing as well as cyber security threats.
Our team will use OpenStreetMap in order to model the distribution of power in a hypothetical Micro-Grid and compare the results to existing models. Transmission and Relay supervision can be modeled and verified in UPPAAL. And the application of Matlab's Simulink and Simevent could come into use when analyzing human decision making through the use of smart meters. The idea is to isolate a fault as soon as possible to minimize the negative impact of the fault on the grid and to distribute energy where it is needed.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: Validation and Verification of Packaging Strategies for
Humanitarian Aid/Disaster Relief (HA/DR) Response
Author: Deneen Gaynor and Nathan Desloover
Abstract: In our previous semester's work we determined the inputs that would help to determine optimal packing arrangements and strategies for responding to HA/DR situations. Speed is always the key to providing the best response, but can also result in the changing of requirements and environmental conditions en route. These factors, combined with the fact that the “product” will always change with the situation, makes it hard to validate and verify the system.
We will look at strategies for optimally translating textual inputs to supply arrangement outputs. Optimizing the logical analysis of requirements combined with spatial arrangement to create a verifiable model for emergency response cargo.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: Water Distribution System Security
Author: Jennifer Light and Lucas Parker
Abstract: This project will evaluate the safety critical components of a water distribution system and create a model for verifying system effectiveness. Having a sufficient, reliable, source of clean water is essential for human health and wellness. However; because a water distribution system involves complex flows of physical and informational goods, this opens the door for potential water security issues. As water moves through the chain from the source to the end usage point, it passes through many different pipelines, treatment centers, distribution centers, etc. It is critical that all these components are looked at from a security perspective in order to maintain our water supply.
This project will identify potential water security risks, and develop a model to show where security practices can help mitigate water security risks. This model will be used to verify that the system is operating under safe conditions and without tampering.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title:
Validation and Verification for Unmanned Underwater Autonomous Vehicles
Author: Jessica Lieberman and Joshua Levine
Abstract: Exploding population levels and the subsequent dramatic rise in energy requirements will soon force mankind to search for solutions offshore. With oil and gas exploration moving farther offshore it is becoming increasingly harder and more costly for companies to maintain their installations. In Brazil, where many oil fields are as far as 400 miles offshore, Petrobras recently sponsored a project for architecture students at Rice University to create conceptual designs for floating cities meant to house oilrig workers. While efforts such as that are steps in the correct direction, those plans fail to take into account the most basic part of city planning; design and development of the backbone infrastructure that population centers are based on. For a population center to be sustainable it must include means of distributing power and communication to the inhabitants. In addition this backbone infrastructure needs to be reliable, robust and easily maintainable.
Our project for the ENSE622 course suggested a design for distributed backbone infrastructure services comprised of power, communication and automated Inspection, Repair and Maintenance (IRM) based on Unmanned Underwater Autonomous Vehicles (UUAVs). That project developed and derived the requirements necessary to detail the aforementioned system in order to support the oil and gas industry in the near term and lay the ground work for the development of self-sustaining large offshore population centers in the future.
This project will continue the effort from that project by using Systems Engineering to develop a feasible Verification and Validation plan for the UUAV infrastructure system.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: A Framework For Natural Language Processing in Requirements Engineering
Author: Edward Carney
Abstract: Significant work has been done to apply natural language processing (NLP) to the domain of requirements engineering. Applications range from using NLP to extract ontologies from a requirements specification, to using NLP to verify the consistency and/or completion of a requirements specification. For this project I will investigate the applicability and challenges associated with incorporating NLP into requirements engineering, and propose a framework for its inclusion.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: Verification and Validation of Parcel Router System
Authors: Abubakr Eltayeb and Sasha Abdalla
Abstract: The Parcel Router system is a system that automatically sorts parcels in chutes using sensors and gates. Through gravity the parcel, once it is dropped at the top of the router, falls through the chutes. Each parcel has a destination code or color that can be detected by sensors. The system will route the parcels to its desired destination.
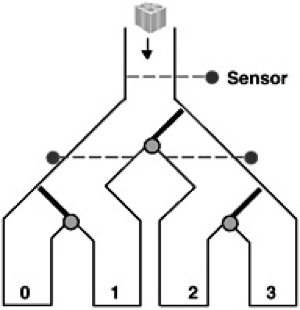
Figure 4. Parcel Router System.
Our project is to develop a system model, investigate its properties and verify and validate it, through various applicable tools, such as LTSA and UPAAL. This particular routing system has limitations. The switches or gates can only move when there is no parcel in the way. Therefore, when multiple packages with different destinations are dropped close to one another, the system will not route correctly. Since the switches will not move quickly enough. Our project will attempt to answer the following question: How much time between dropped parcels (different colors) before the system fails? Using the developed system model, failures in the system will be interpreted to its corresponding physical properties, hence proposing solutions to the problem.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Title: JUnit Testing for a Predictive Analytics System
Author: Jeremy Feldman
Abstract: The goal of this project is to write JUnit tests to verify and validate a Predictive Analytics System Module. A traditional analytics system is used for the discovery and communication of meaningful patterns in data. Analytics is essential for businesses and traditionally requires a human in the loop to go from analytics report to understanding or making a decision based on that report. Predictive Analytics adds a layer of intelligence to this feedback and understanding process. It requires a real time system and learning algorithms that allow the technology to learn from experience (data) to predict people's further behavior in order to drive better decisions, with obvious commercial benefits.
The system that will be studied is a single module from a larger module based predictive analytics system. JUnit, a java unit-testing framework will be used to verify and validate that the requirements for this system align with its operation in a testable way.
References
Midterm Presentation: Scheduled for October 28
Class Presentation: Scheduled for ....
Developed in October 2014 by Mark Austin
Copyright © 2014, Institute for Systems Research, University of Maryland