News Story
Work by Srivastava, Liu wins Best Paper Award at the 2020 ACM Cloud Computing Security Workshop
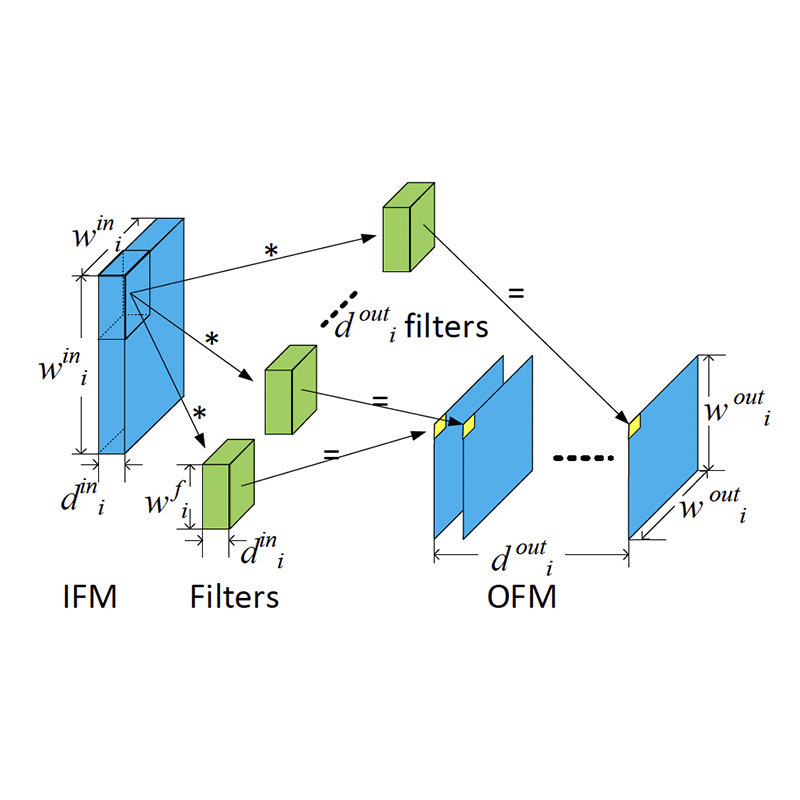
Illustration of a Conv layer. “*” indicates inner product, each computing an output neuron. (Fig. 1 from the paper)
GANRED: GAN-based Reverse Engineering of DNNs via Cache Side-Channel has won the Best Paper Award at the ACM Cloud Computing Security Workshop (CCSW 2020), held online Nov. 9, 2020. The paper was written by ISR Director and Professor Ankur Srivastava (ECE/ISR) and alumnus Yuntao Liu (ECE Ph.D. 2020). Liu, Srivastava’s former Ph.D. student, now works for him as a postdoctoral researcher.
In recent years, as deep neural networks (DNN) have become an important type of intellectual property due to their high performance on various classification tasks, DNN stealing attacks have emerged and many attack surfaces have been exploited. Cache timing side-channel attacks are hugely problematic because they do not need physical probing or direct interaction with the victim to estimate the DNN model.
Existing cache side-channel-based DNN reverse engineering attacks rely on analyzing the binary code of the DNN library that must be shared between the attacker and the victim in the main memory. However, in reality, the DNN library code is often inaccessible because the code is proprietary, or memory sharing has been disabled by the operating system.
In their paper, Srivastava and Liu propose GANRED, an attack approach based on the generative adversarial nets (GAN) framework which utilizes cache timing side-channel information to accurately recover the structure of DNNs without memory sharing or code access.
With GANRED, there is no need for DNN library code analysis and no shared main memory segment needed between the victim and the attacker. The GANRED attack can locate the exact structure of the victim model, unlike existing attacks which only narrow down the structure search space. In addition, this new attack efficiently scales to deeper DNNs, exhibiting only linear growth in the number of layers in the victim DNN.
GANRED’s Prime+Probe method only requires minimal resources and is successful and scalable. GANRED produces more accurate results than existing attacks, possibly because the cache side-channel information used by GANRED inherently contains more information, including about the DNN’s overall memory pattern. Such attacks must be considered when the intellectual property of a DNN is concerned.
The CCSW workshop is the world's premier forum to bring together researchers and practitioners in all security aspects of cloud-centric and outsourced computing. The workshop is held in conjunction with the ACM Conference on Computer and Communications Security (CCS 2020).
Published November 11, 2020









